Best Describes the Concept of a Vlan
- Devices on the same network logically grouped as if they were on separate networks. Which answer best describes how the concept of liberty influenced eastern europe.
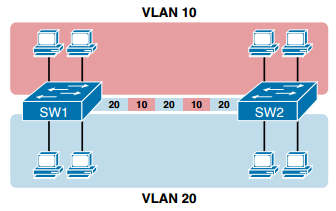
Ccna Dc Faq Vlan And Trunking Concepts Config Router
Which of the following best describes the concept behind web 20.

. You will never regret it. Which of the following best describes the concept of audit risk. - Devices on the same network logically grouped as they were on separate networks.
Which of the following best describes the concept of a VLAN. A broadcast domain is a network segment in which if a device broadcast a packet then all the devices in the same. Devices on the same network logically grouped as if they were on separate networks.
This article will explain VLANs from a practical perspective. Make the following of the smart choices when setting up VLANs. Devices on the same network logically grouped as if they were on separate networks.
Which of the following is not one of the steps in implementing the marketing concept. Virtual LAN VLAN is a concept in which we can divide the devices logically on layer 2 data link layer. Which statement best describes StaticPort Centric VLANs.
Which of the following best describes the concept of VLAN. VLAN assignment depends on the port a device connects in c. VLAN in networking are identified by a number.
Which of the following best describes the concept of a pocket veto. VLANs that you dont want on the trunk should be excluded. A Valid range is 1-4094.
Generally layer 3 devices divide broadcast domain but broadcast domain can be divided by switches using the concept of VLAN. Which of the following best describes the concept of federalism. VLAN increase the numbers of broadcast domain while reducing their size.
You manage a network with two switches. VLAN hopping is a brute force attack executed to gain additional access. Which of the following BEST describes the concept of a VLAN-Devices on the same network logically grouped as if they were on separate networks.
Session hijacking involves physically disrupting a. - Devices connected through the internet that can communicate without using a network address. Rarely used as it needs a lot of time and effort to setup b.
Which one of the following best describes the concept of erosion. Router Hub Bridge Switch. Finally at the end of the article is a two question.
Which of the following statements accurately describes a. Use firewalls to create a DMZ. Which of the following identifies the vlan to which each piece of data belongs.
Which of the following statements best describes the concept of operant conditioning. Which of the following best describes the concept of federalism. Which of the following statements accurately describes a vlan id.
Devices connected through the internet that can communicate without using a network address. VLAN is defined as a custom network which is created from one or more local area networks. The VLAN that is assigned this port should be labeled Untagged.
Which of the following BEST describes a VLAN hopping attack. VLAN management is something you all must have a grip on for your organizations security. The switches are connected together through their Gigabit.
Which of the following best describes the concept of a VLAN. Which of the following BEST describes the differences between VLAN hopping and session hijacking. Which of the following connectivity hardware is used to create a VLAN.
Virtual Local Area Networks or VLANs are a very simple concept that has been very poorly defined by the industry. VLAN Basic Concepts Explained with Examples Solve broadcast problem. Devices on the same network logically grouped as if they were on separate networks Your company is a small start up company that has leased office space in the building shared by other businesses.
It is the device on different networks on which various packets are received. Select the statement that best describes the. Which of the following best describes the concept of a virtual LAN.
Use calls to a lookup database for assigning end-devices to VLANs d. On a VLAN switch you assign ports with the proper VLAN number. When we connect devices into the switch ports switch creates separate collision domain for.
Which of the following best describes the concept of audit risk. Which of the following suggestions can help prevent vlan hopping attacks on a network. - Devices connected by a transmission medium other than cable such as microwave or radio transmissions.
The devices are present on the same network but logically linked the way they were working on the separate network. Reduce the size of broadcast domains. Which of the following best describes the concept of a vlan.
Applicable Devices RV042. Virtual LANs offer structure for making groups of devices even. These are the devices that without the use of.
1Devices on different networks that can receive multicast packets 2Devices connected through the internet that can communicate without using a network address 3Devices on the same network logically grouped as if they were on separate networks. Which of the following best describes the concept of virtual LAN. VLANs need to be set up with best practices to keep your network safe and secure.
An attacker gains unauthorized access to a network by placing a rogue AP on the network. Session hijacking involves overriding a user-s web connection to execute commands. Allow us to add.
Each LAN port can be set to be an access port or a trunk port. It will be framed around the two major functions of VLANs and concluded with an explanation of the idea behind the Native VLAN. Which of the following best describes the concept of a VLAN.
Place the Web server inside the DMZ and the private network behind the DMZ Devices on the same network logically grouped as if they were. Which of the following best describes the concept of a VLAN. To another to gain additional access.
Best Practice 1 - VLAN Port Assignment Port Assignment Basics. One VLAN assigned on a LAN port. Which graphic concept best illustrates the concept of social stratification.
An attacker gains unauthorized access to a network by using double-tagged packets. 525 students attemted this question. Which of the following best describes the concept of VLAN.
Devices on the same network logically grouped as if they were on separate networks. Which of the following best describes the concept of a vlan. Devices connected by a transmission medium other than cable such as microwave or radio transmissions.
An attacker gains unauthorized access to a network by overflowing the CAM table. Configuring Access Ports. Which of the following best describes the concept of a vlan.
A VLAN can be placed in more than one port. Which of the following statements accurately describes a vlan id General. Which one of the following best describes the concept of erosion.
When configuring VLANs on a switch what is used to identify VLAN membership of a device.

Concept Of Native Vlan With Configuration Example The Network Dna

What Is A Vlan What Is A Vlan Huawei

6 1 2 7 Packet Tracer Investigating A Vlan Implementation Premium It Exam Answers
Comments
Post a Comment